Introduction
What is "WASTE again"?
"WASTE again" enables you to create a decentralized and secure private mesh network using an unsecure network, such as the internet. Once the public encryption keys are exchanged, sending messages, creating groupchats and transferring files is easy and secure.
Creating a mesh
To create a mesh you need at least two computers with "WASTE again" installed. During installation, a unique pair of public and private keys for each computer is being generated. Before the first connection can be established, you need to exchange these public keys. These keys enable "WASTE again" to authenticate every connection to other "WASTE again" clients.
After exchanging the keys, you simply type in the computers IP address to connect to. If that computer is located behind a firewall or a NAT-router, you have to create a portmap first to enable incoming connections.
At least one computer in your mesh has to be able to accept incoming connections, making it a "public node". If no direct connection between two firewalled computers can be made, "WASTE again" automatically routes your traffic through one or more of the available public nodes.
Every new node simply has to exchange keys with one of the connected nodes and then connect to it. All the other nodes will exchange their keys automatically over the mesh.
Example of a centralized network
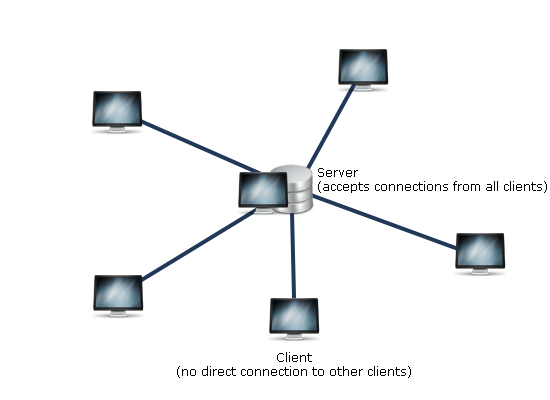
The approach of a centralized server uses one or more servers that manage the dataflow for all the clients. Its very efficient and scalable but also very prone to attacks since the network stands and falls with the server.
Running WASTE with only one node accepting incoming connections basically is a centralized network but as soon you add more public nodes, it becomes a decentralized mesh.
Example of a decentralized mesh
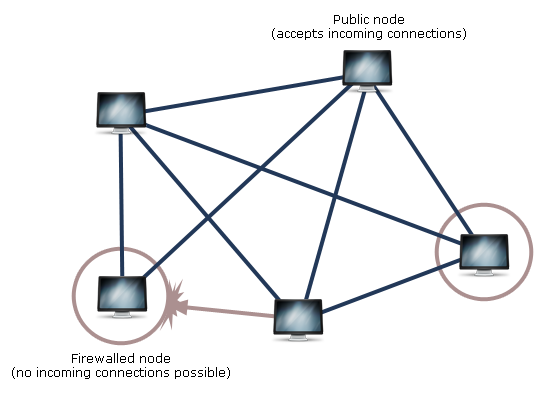
This approach uses all its nodes as servers as well as clients. In theory, everyone can connect to everyone else, making a centralized server unnecessary. Its very robust against attacks but not very scalable.
Since there may be no known, fixed adress on the mesh, there may be the problem of finding the first node to connect to. This problem is adressed by making "WASTE again" remember the last few IP-adresses it was connected to. This technique works well for mid-sized meshes where there is at least one IP accessible that your client remembers "from last night". It may still be insufficient in situations where there aren't enough clients on the mesh to keep reliable set of last known IP-adresses.
Security
"WASTE again" uses link-level encryption (opposed to end-to-end encryption). It means that all the data on the mesh is always readable by everyone in your mesh but not readable from outside the mesh.
This also means that it is required that you can trust each and everyone in your mesh since it is possible to easily sniff or spoof messages.
To prevent information leakage inside the mesh, all versions from "WASTE again" 1.7.2 on up support "encrypted messaging". Encrypted messaging transmits point-to-point-encrypted messages within the mesh itself, enabling only the originator and the designated recipient to read the contents of the message.
To prevent attackers from suggesting the amount of data being moved on your mesh, "WASTE again" features a link saturation feature. On a saturated link, "WASTE again" transmits random waste when there is not real data to be transmitted.
Whats the difference to original "WASTE"?
"WASTE again" is a fork of the original "WASTE" project whose development has been presumably dead for several years now. It aims at improving the capabilities of "WASTE" by adding features or fixing long known problems. The "WASTE again" 1.7-series is fully compatible to all original WASTE clients and meshes.
Please note that the experimental 16k-build can not send or download files to or from any legacy WASTE or WASTE again clients (chatting however is still possible)!
